2.2 Secure Boot
Secure boot is a program that verifies the digital signature of files and applications using the corresponding public keys to ensure the integrity and authenticity of the boot file or program, to prevent unauthorized programs from being loaded and running during the boot process.
Under the secure startup mechanism, all startup files (e.g., the bootloader, kernel image, baseband firmware) must pass signature verification before they are allowed to load and run. If the signature verification fails at any stage during the boot process, the process will be terminated.
The ROM SoC Bootloader is written into a chip's internal ROM when the chip is manufactured, and cannot be modified after leaving the factory. This piece of code is the first to be executed after the device is powered on.
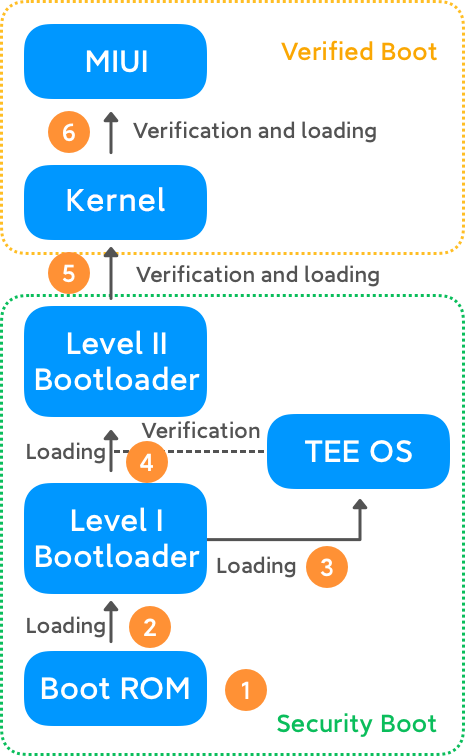
When the device is powered on, the PC pointer points to the Boot ROM address inside the chip, and the process is executed.
The Boot ROM is loaded from an external storage device, and the level I Bootloader gets executed after verification.
The level I Bootloader loads the TEE OS image file.
The level I Bootloader loads the level II Bootloader, and then the TEE OS verifies its integrity.
The level II Bootloader verifies and loads the kernel file.
The kernel program verifies and loads the MIUI system.
After the device is powered on, the ROM SoC Bootloader will first perform the basic system initialization and load the level I bootloader from the Flash memory chip. It will then utilize the public key stored in the FUSE space inside the main chip to verify the digital signature of the level I bootloader image. The level I bootloader will run after successful verification.
After completing the above steps, the level I bootloader will load, verify and execute the TEE OS image. Once the TEE OS is in operation, it will verify, load and execute the level II bootloader together with the level I bootloader. Such a process will continue until the entire system startup is completed to ensure the chain of trust is transferred during the boot process and prevent unauthorized programs from being maliciously loaded and run.
MIUI system supports Android's Verified Boot 2.0 (AVB2.0) feature. Before entering any subsequent stage in a device's startup process, code reliability must be verified through an authenticated encryption process to ensure that all components—from the hardware-protected root of trust to the bootloader and boot partition or other verified partitions (including system, vendor and optional OEM partitions)—are free from any known security defects. AVB helps prevent persistent rootkit from holding root privileges and ensures the security of the device during the startup process.