4.1 Application Security Protection
4.1.1 Signature
The figure below shows the process of the new application signature.
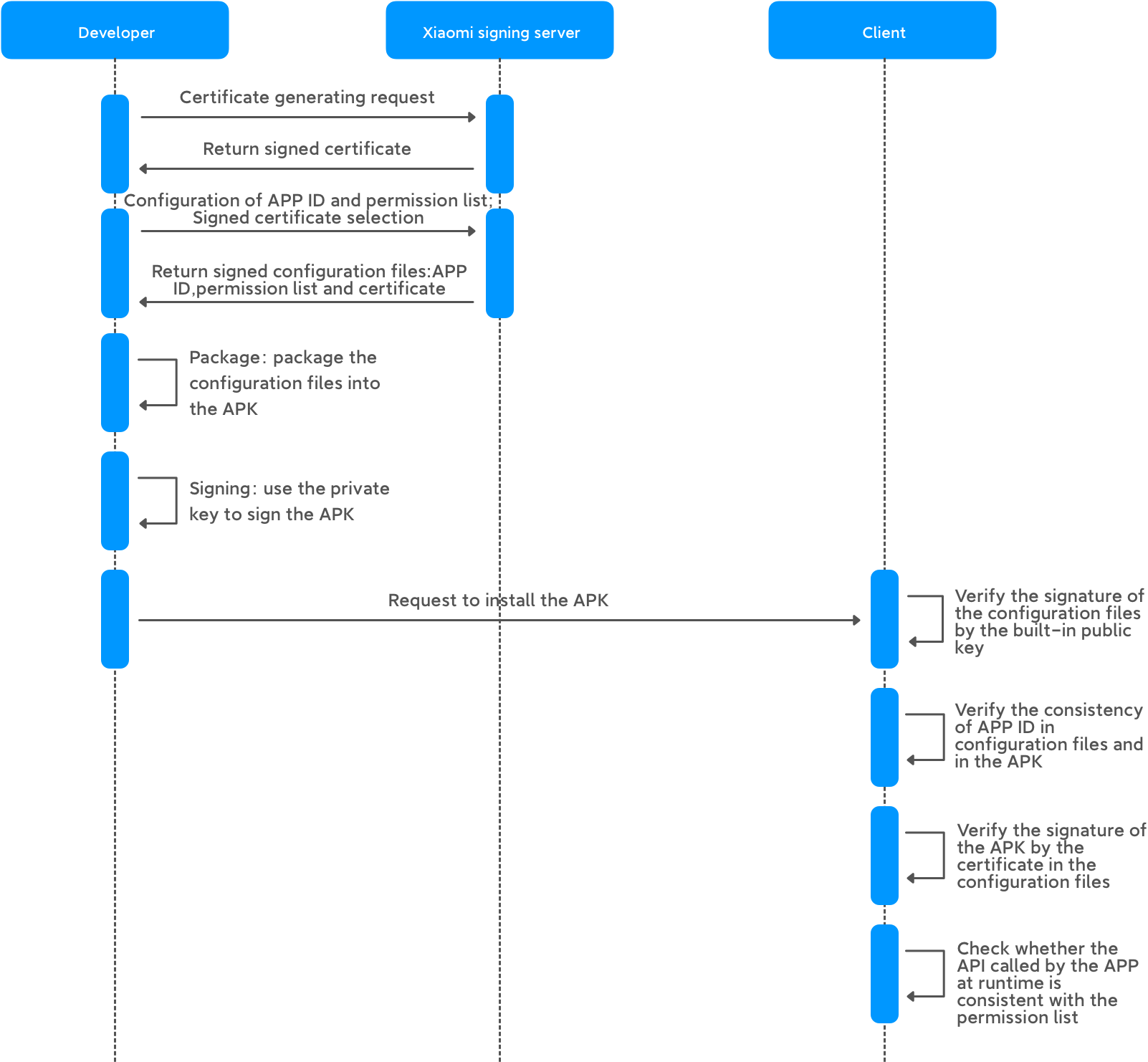
MIUI verifies the integrity of the application package (hereinafter referred to as "APK") and the officialness of its source in order to:
1) Ensure that the APK is tamper-proof
The developer generates the public key and the private key, signs the APK with the private key, and packages the public key into the APK. When the application is installed, the public key is used to verify that the APK has not been tampered with.
When updating the installed application, the application signature verification is also required. Only applications with the same signature as the updated application are allowed to be updated, to prevent malicious applications from replacing existing ones.
2) Ensure that the APK is forgery-proof
The APP ID of the APK and the certificate used to verify the signature are signed with the official private key. If developer A signs developer B's APK with its certificate and packages this certificate file into the APK, the official signature verification will fail when developer A uploads it to the application store.
3) Ensure that APK permissions cannot be changed at will
The authorization list, APP ID and certificate are all signed with the official private key. When installing and running the application, check the consistency of the authorization list and the system service it revokes, if these are not consistent, the MIUI service being invoked will fail.
4.1.2 Runtime Protection
MIUI supports Android's native Address Space Layout Randomization (ASLR) and Data Execution Prevention (DEP). ASLR is a security technique that protects against buffer overflow. It randomizes the layout of linear areas such as heaps, stacks and shared libraries, making it harder for attackers to predict target addresses and preventing them from locating attack codes, thereby preventing overflow attacks. ASLR makes it more difficult for attackers to take advantage of memory vulnerabilities. DEP marks specific memory areas as non-executable to prevent attacks exploiting memory vulnerabilities.
In addition, MIUI also uses the native Android application sandbox mechanism to ensure that each application runs in the sandbox and is isolated from each others, thus ensuring the security of the runtime application.
4.1.3 Application Security Detection
Xiaomi GetApps conducts automatic testing, security scanning and manual review for each application to ensure the security of the application's source. If you download apps from unknown sources, your phone and personal information can be at risk. On the MIUI devices, we recommend that you get apps from Xiaomi GetApps or Google Play.
For the device, MIUI provides system protection and detection mechanisms such as virus scanners and removers embedded with various antivirus engines and application installation monitors.
In addition, the "Security"-"Solve problems" feature also provide ROOT security detection and anomaly detection in terms of mobile phone performance, operation and power consumption.
The following functions are included:
- Performance anomaly detection: This feature detects whether the app has enabled accessibility and device manager and whether the device's remaining memory is insufficient.
- Network & Setting anomaly detection: This feature detects whether the device has enabled flight mode, call blocking (for contacts and unknown callers), DND mode and eye protection mode.
- Battery anomaly detection: This feature detects whether there are too many autostart applications (more than 5) and whether the hotspot feature has been enabled.
- Other anomaly detection: This feature detects whether the system is rooted, and notifies the user that the application cannot be installed when the storage space is less than 5%.